
PDF 和文档安全对贵公司有多重要?
在很多情况下,您都应该确保重要文件受到保护。同时,您还需要能够与需要查看这些文件的人共享这些文件。.
安全漏洞会给公司带来灾难性后果。敏感信息可能会帮助竞争对手获得优势,机密数据的泄露可能会造成严重的声誉损害,或者在 HIPAA 和 GDPR 等合规框架下被处以罚款。公司需要考虑数据泄露可能带来的法律后果,包括知识产权的滥用。.
什么是文件安全?
文档安全包括几种不同的措施,旨在保护访问并阻止对 PDF 或其他类型文档的不当使用。.
通常采用的安全措施有
- 密码保护
- 水印
- 文件过期、自毁和访问限制
- 数字版权管理:限制复制、打印或转发
- 对浏览者进行文件跟踪
PDF 密码保护
密码保护是任何人保护 PDF 或其他类型文件的最简单措施之一。虽然密码绝不是一个完美的安全系统,但它为任何试图不正当访问文档的人提供了额外的保护。.
有时,人们会无意中接触到文件,或者在其他时候,有人会故意试图访问他们不应该看到的文件。考虑到办公环境中的共享文件夹或共享计算机等情况,你就能明白文件可能会如何超出预想的范围。.
文件密码的传送可能是一个有点麻烦的步骤。通常,你会通过一种方式发送文件本身,然后通过另一个渠道发送密码。当然,根据你使用的通信渠道,密码有可能会被传播得更远,而且没有什么能阻止别人与他人共享密码。.
尽管如此、, 用密码保护 PDF 这是您可以采取的阻止不正当文件访问的最简单步骤之一,与其他安全措施结合使用尤其有效。.
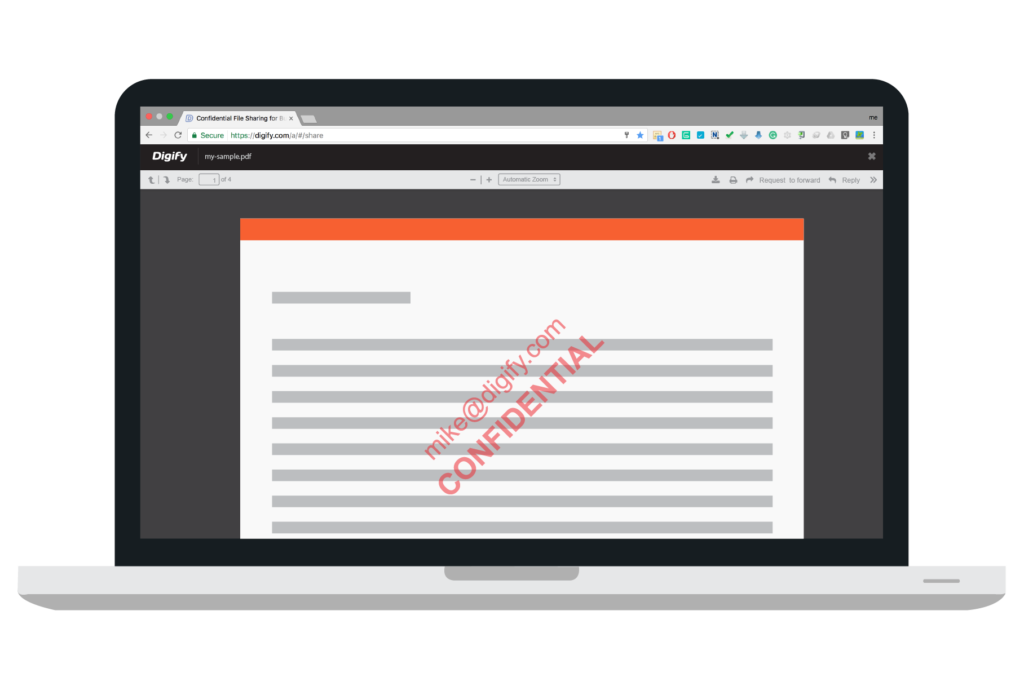
水印
早在 13 世纪就已发现的原始文件安全措施之一是 文件水印. .传统上,水印一直被用于主张所有权或作为文件的商标装置,但在数字意义上,水印还有更多的应用。.
例如,你可能希望阻止机密文件的泄漏,并在这些文件传播得比预期更远时,提供一些可追溯性手段。一种策略是在数字文件上打上收件人自己电子邮件地址的水印,从而提供泄漏源。.
第二种更基本的应用是传达文件分类,让收件人知道如何处理该文件。与没有水印的文件相比,有人在处理带有 “机密 ”水印的文件时可能会更加小心。.
第三,水印仍可用于传统意义上的文件所有权声明。.
文件过期和自毁
有很多可能的应用情况,你可能想撤销对文档的访问权限,或者限制文档的访问权限,使文档的接收者无法永久获得该文档。例如,请考虑这些可能的情况:
- 一名员工离开了公司,或者与承包商的关系出现了问题。您要确保他们无法再访问潜在的敏感文件。.
- 您有一个项目,在此期间需要访问敏感信息,但您不希望持续访问这些信息。.
- 您有一份合同或竞标正在进行中,而报价只在规定时间内有效。您不希望截止日期一过就无法获取报价。.
- 您想防止链接在下载文件后被重复使用。.
所有这些情况都可以使用 文件过期, 此外,还具有撤销访问权限和自毁功能。事实上,许多公司更愿意将这些访问限制作为文件管理实践的正常组成部分,因为否则,一旦文件被发送出去,往往就完全失去了对它的控制。.
同样,这些类型的功能在与一个或多个其他安全功能结合使用时,往往能大大提高文件的安全性。.
数字版权管理(DRM)
数字版权管理(DRM)可以控制读者对文档的操作。DRM 通常适用于包含敏感信息或知识产权的文档,文档所有者不希望这些信息或知识产权被复制或传播。.
例如,如果您编写了一门课程或电子书,您就需要保护自己的知识产权,以确保不会有人复制并从中获利。如果您有机密文件需要发送以进行尽职调查,那么您需要确保这些文件不会发送到预定收件人以外的地方。.
比如密码保护、, DRM 是防止文件轻易传播的有效屏障。你可以防止打印,这样就不会意外地将打印副本留在别人可以找到的地方,而这种情况在公司中经常发生。您还可以阻止他人复制文档并将其粘贴到电子邮件或新文档中。这意味着,如果有人想窃取你的知识产权,他们将面临更困难的任务。.
文件跟踪
您有多少次在发送文件后,能够确定谁看过、打开过多少次以及从哪里打开的?经常发生的情况是,一旦文件发送出去,文件所有者就失去了控制权--任何人都可能查看你的数据,而你却毫不知情。.
这就是 文件跟踪 是一项重要的安全功能。PDF 文件和文档跟踪解决方案可帮助您了解文档的移动情况,以及它们是否超出了您的预期受众范围。您可以查看文档从何处打开等信息,并注意是否存在可疑活动。如果您采取了其他措施(如撤销访问权限),您就有可能对此采取一些措施。.
在下列情况下应考虑文件跟踪
- 安全问题。您可能正在传输敏感信息,因此需要格外小心文件的传输距离。.
- 销售和营销。如果跟踪打开情况,就可以衡量文档的受欢迎程度。在向某人发送推销信息等情况下,您可以检查对方是否已经看到,然后找出合适的时间进行跟进。.
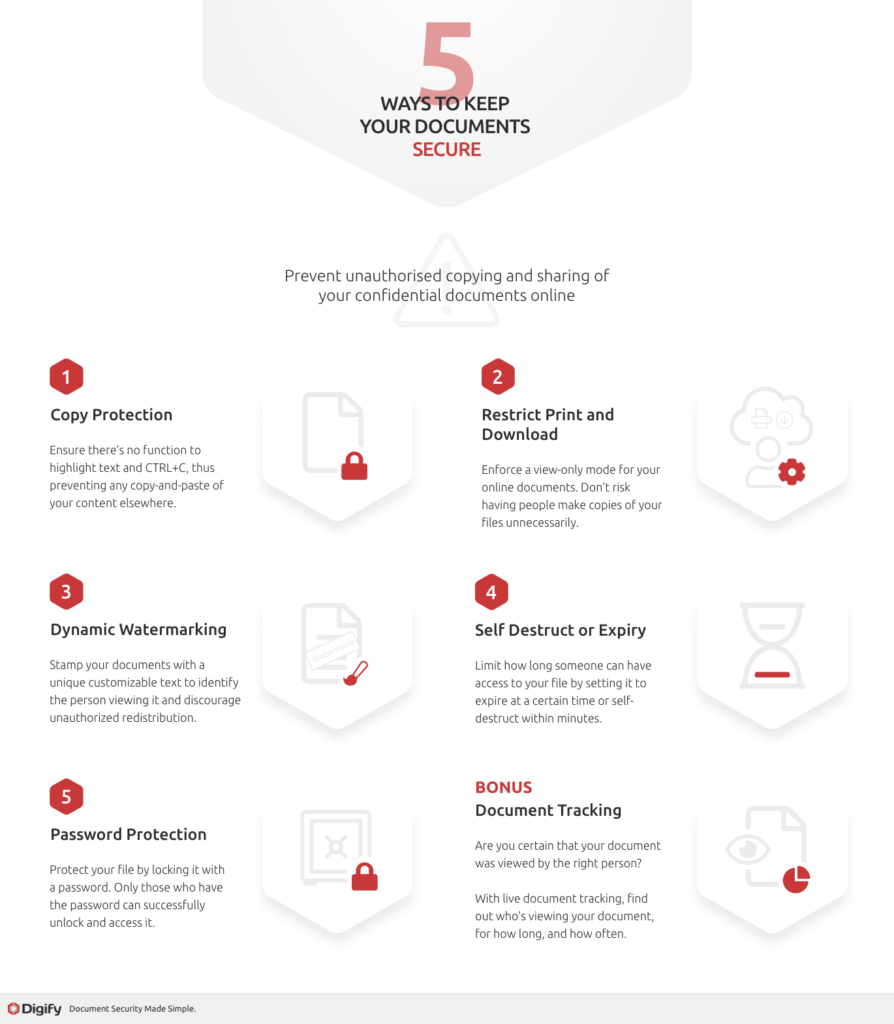
查看下面的信息图表,了解确保文档安全的五种最佳方法。.

Willy Cheah
作者
营销专家,专注于将洞察力转化为可衡量的业务影响。.
您可能还喜欢



